Understanding Azure policies
Azure Policy is a mechanism for effecting organizational compliance on the Azure platform. The service allows aggregated views to understand the overall state of an environment, with the ability to view resource-level granularity for compliance. All this can be viewed on the compliance dashboard. Remediation can be applied automatically and through bulk operations.
The following screenshot illustrates an example policy overview for an organization:
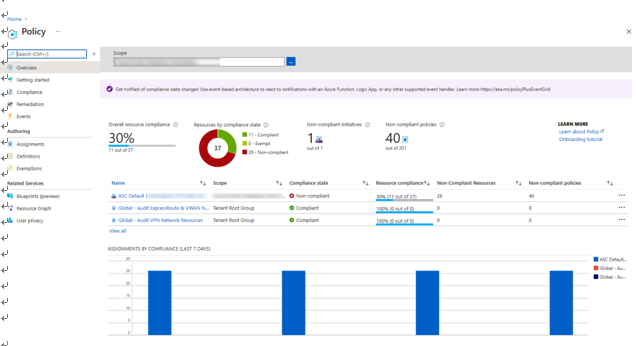
Figure 3.1 – Azure policy example
As you will observe, this is where we will create and manage policies, as well as get an overview of compliance for policies that you have implemented in Azure.
How does Azure Policy work?
Azure Policy assesses compliance by comparing resource properties to business rules defined in a JavaScript Object Notation (JSON) format. These are known as policy definitions.
A policy initiative is a grouping of definitions that align with business objectives such as the secure configuration of virtual machines (VMs). This could contain a policy to assess antivirus compliance and a policy for assessing disk encryption compliance, as well as other policies.
Azure Policy resides above the subscription and management group layers, and it can therefore be assigned to various scope levels—an individual resource, resource group, subscription, or management group. Thisis defined as policy assignment or scope.
Azure Policy versus RBAC
Both Azure Policy and role-based access control (RBAC) contribute to controlling governance within Azure. While both create methods of controlling access, there is often confusion between the two. We distinguish the difference between them for clarity, as follows:
- Azure Policy focuses on resource properties for existing resources and resources being deployed.
- RBAC focuses on user actions at different scopes.
Working with Azure Policy
Azure offers predefined built-in policies, as well as an option to create custom policies.
The same applies to initiatives, which we will explore in this section.
Some examples of built-in policies include the following:
- Allowed virtual machine size SKUs: This policy specifies a set of VM sizes and types that can be deployed in Azure.
- Allowed locations: This policy restricts available locations where resources can be deployed.
- Allowed resource types: This policy defines a list of resource types that can be deployed. Resource types that are not on the list can’t be deployed inside the Azure environment.
- Not allowed resource types: This policy prevents certain resource types from being deployed.
- Require a tag and its value on resources: Enforces a required tag and its value. Does not apply to resource groups.
If the built-in policies don’t meet your desired requirements, you can create a custom policy instead. Custom policies are created in JSON, with the code defining several properties. When creating in the portal, the second part defines policy rules (which are usually just extended in the same JSON file).
The following code is an example of a policy definition:
{
“properties”: {
“displayName”: “Deny storage accounts not using only
HTTPS”,
“description”: “Deny storage accounts not using only HTTPS. Checks
the supportsHttpsTrafficOnly property on StorageAccounts.”, “mode”: “all”,
“parameters”: {
“effectType”: {
“type”: “string”,
“defaultValue”: “Deny”,
“allowedValues”: [
“Deny”,
“Disabled”
],
“metadata”: {
“displayName”: “Effect”,
“description”: “Enable or disable the execution of the policy”
}
}
},
In this part of the code, we are looking at the policy rule:
“policyRule”: {
“if”: {
“allOf”: [
{
“field”: “type”,
“equals”: “Microsoft.Storage/storageAccounts”
},
{
“field”:
“Microsoft.Storage/storageAccounts/supportsHttpsTrafficOnly”,
“notEquals”: “true”
}
]
},
“then”: {
“effect”: “[parameters(‘effectType’)]”
}
}
} }
As you will notice, the preceding policy assesses Azure storage accounts and identifies if the configuration for HyperText Transfer Protocol Secure (HTTPS)-only communication is set to true. Where it does not comply, then the configured effect will be enforced based on what is entered for the parameter sections.

